Playbook: Delete Detected Files
Description
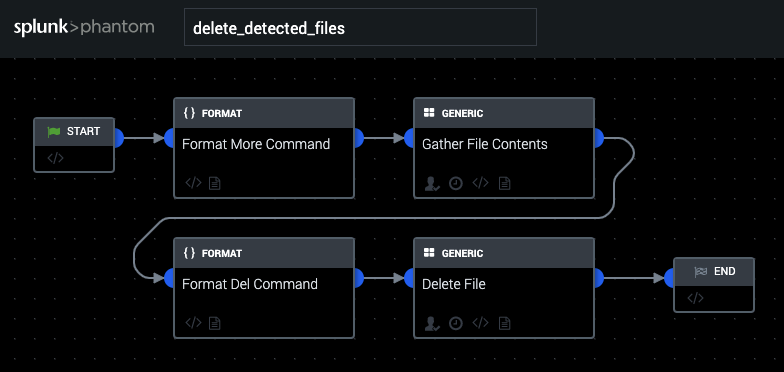
This playbook acts upon events where a file has been determined to be malicious (ie webshells being dropped on an end host). Before deleting the file, we run a "more" command on the file in question to extract its contents. We then run a delete on the file in question.
Apps
How To Implement
This playbook reads and then deletes files stored with artifact:.cef.filePath from hosts stored in artifact:.cef.destinationAddress. Windows Remote Management must be enabled on the remote computer.
Explore Playbook
Required fields
-
filePath
-
destinationAddress
Reference
source | version: 1
