Email Notification for Malware
Description
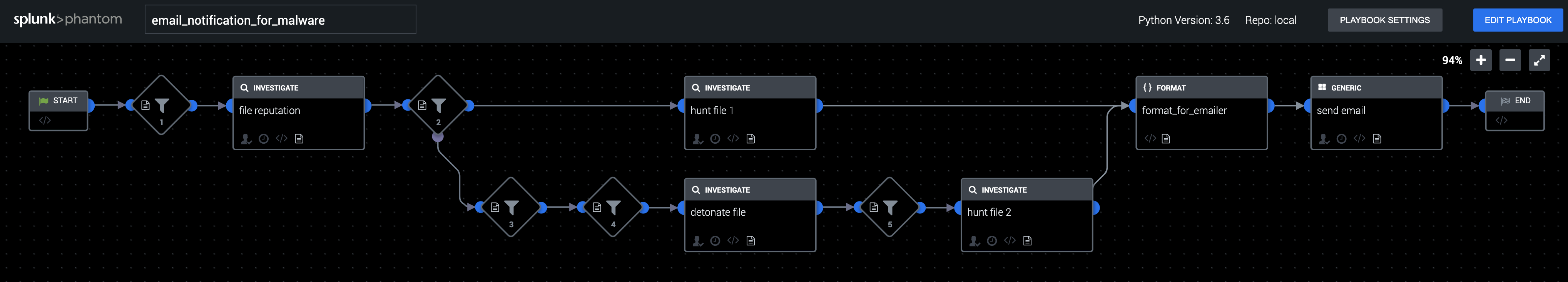
This playbook tries to determine if a file is malware and whether or not the file is present on any managed machines. VirusTotal "file reputation" and PAN WildFire "detonate file" are used to determine if a file is malware, and CarbonBlack Response "hunt file" is used to search managed machines for the file. The results of these investigations are summarized in an email to the incident response team.
- Type: Response
- Product: Splunk SOAR
- Apps: VirusTotal, WildFire, Carbon Black Response, SMTP
- Last Updated: 2021-01-19
- Author: Philip Royer, Splunk
- ID: fb3edc76-ff2b-48b0-5f6f-63da6483fd63
- Use-cases:
Associated Detections
How To Implement
Be sure to update asset naming to reflect the asset names configured in your environment.
Explore Playbook
Required field
- fileHash
- vaultId
Reference
source | version: 1