Hunting
Description
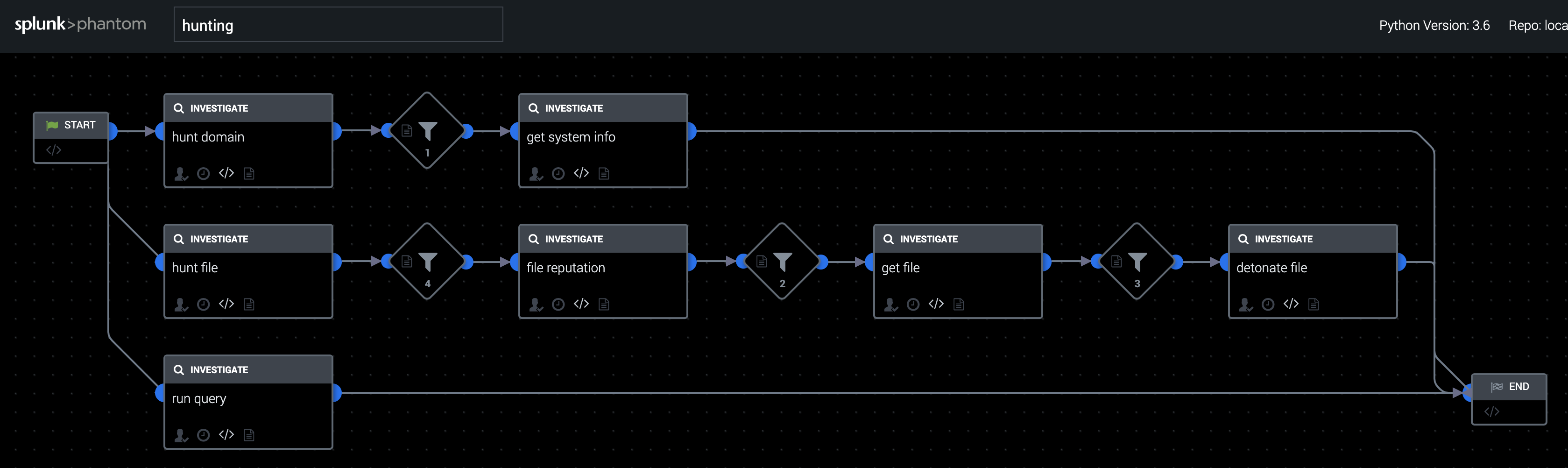
The hunting Playbook queries a number of internal security technologies in order to determine if any of the artifacts present in your data source have been observed in your environment.
- Type: Investigation
- Product: Splunk SOAR
- Apps: Splunk, Reversing Labs, Carbon Black Response, Threat Grid, Falcon Host API
- Last Updated: 2021-01-21
- Author: Philip Royer, Splunk
- ID: fb3edc76-ff2b-48b0-5f6f-63da6351ad63
- Use-cases:
Associated Detections
How To Implement
Be sure to update asset naming to reflect the asset names configured in your environment.
Explore Playbook
Required field
- fileHash
- vault_id
Reference
source | version: 1