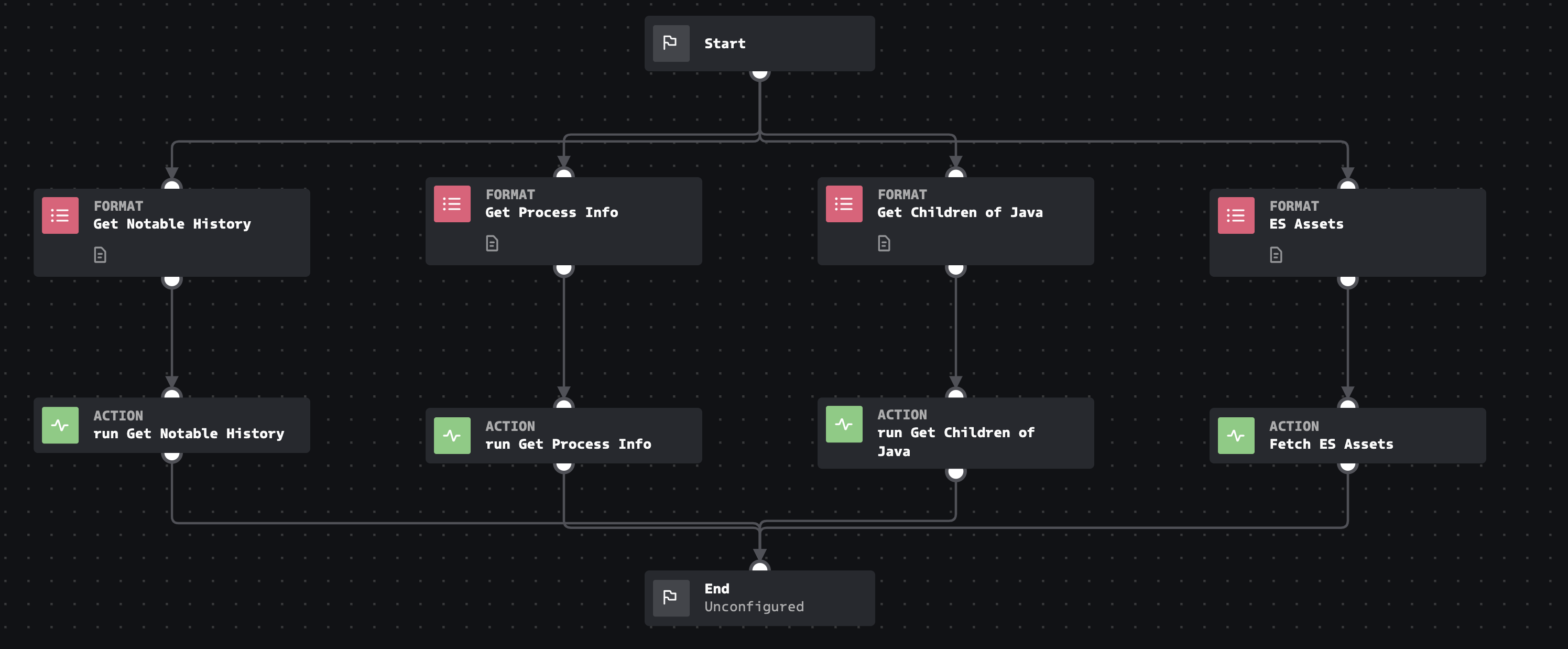
Playbook: Internal Host Splunk Investigate log4j
Description
Published in response to CVE-2021-44228, this playbook utilizes data already in your Splunk environment to help investigate and remediate impacts caused by this vulnerability in your environment.
Apps
How To Implement
This playbook presumes you have Enterprise Security and have configured Assets & Identities, as well as the Endpoint.Processes datamodel
Explore Playbook
Click the playbook screenshot to explore in more detail!
Required fields
-
hostName
-
destinationAddress
Reference
source | version: 1