Internal Host Splunk Investigate log4j
Description
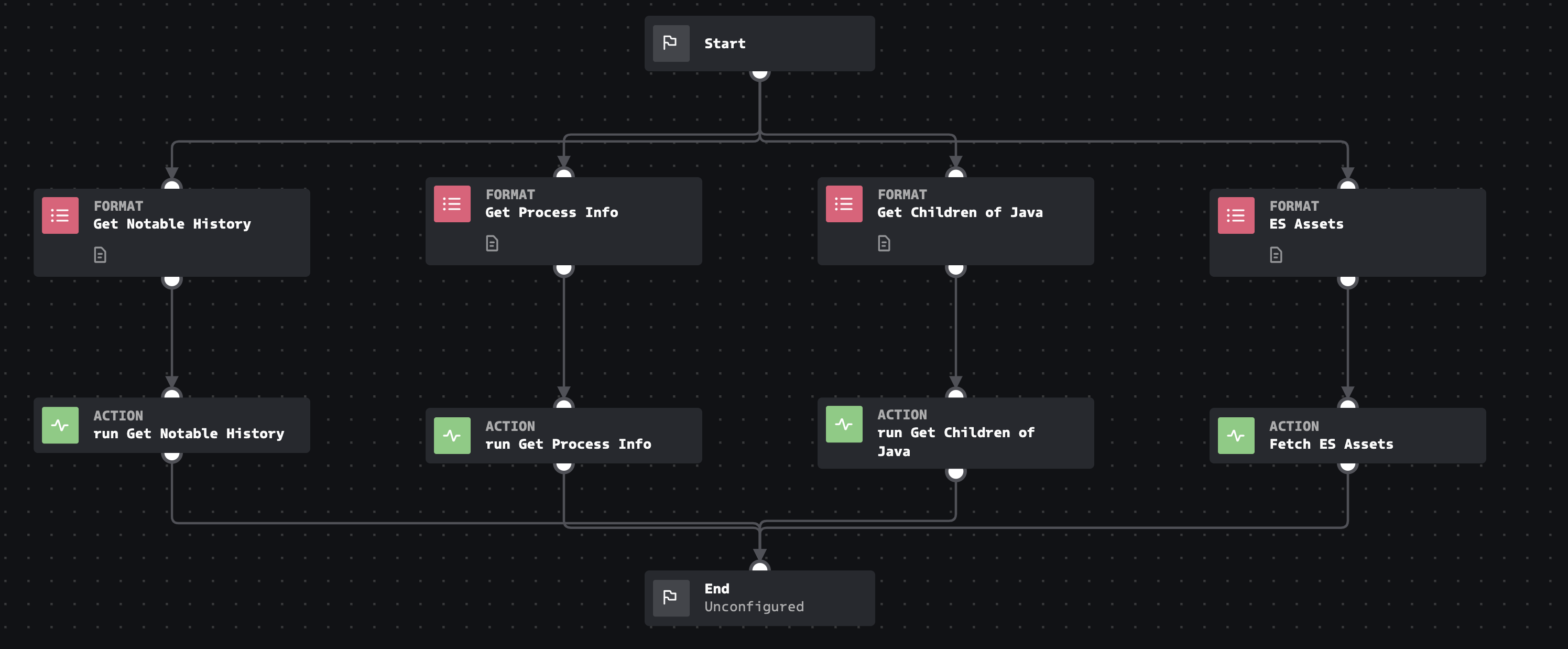
Published in response to CVE-2021-44228, this playbook utilizes data already in your Splunk environment to help investigate and remediate impacts caused by this vulnerability in your environment.
- Type: Investigation
- Product: Splunk SOAR
- Apps: Splunk
- Last Updated: 2021-12-14
- Author: Lou Stella, Splunk
- ID: fc0adc66-ff2b-48b0-9a6f-63da6783fd63
- Use-cases:
Associated Detections
How To Implement
This playbook presumes you have Enterprise Security and have configured Assets & Identities, as well as the Endpoint.Processes datamodel
Explore Playbook
Required field
- hostName
- destinationAddress
Reference
source | version: 1