Ransomware Investigate and Contain
Description
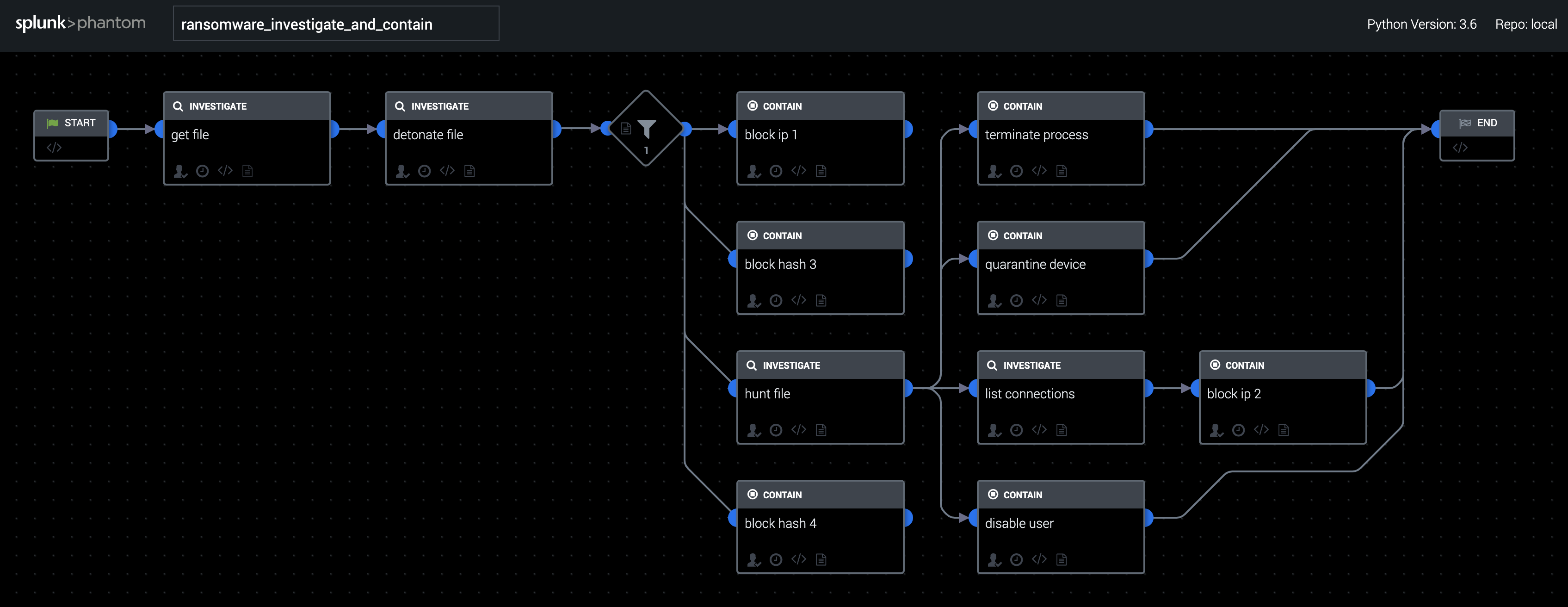
This playbook investigates and contains ransomware detected on endpoints.
- Type: Response
- Product: Splunk SOAR
- Apps: Carbon Black Response, LDAP, Palo Alto Networks Firewall, WildFire, Cylance
- Last Updated: 2018-02-04
- Author: Philip Royer, Splunk
- ID: fc0edc96-ff2b-48b0-9f6f-63da3783fd63
- Use-cases:
Associated Detections
How To Implement
This playbook requires the Splunk SOAR apps for Palo Alto Networks Firewalls, Palo Alto Wildfire, LDAP, and Carbon Black Response.
Explore Playbook
Required field
- ComputerName
- Username
Reference
source | version: 1