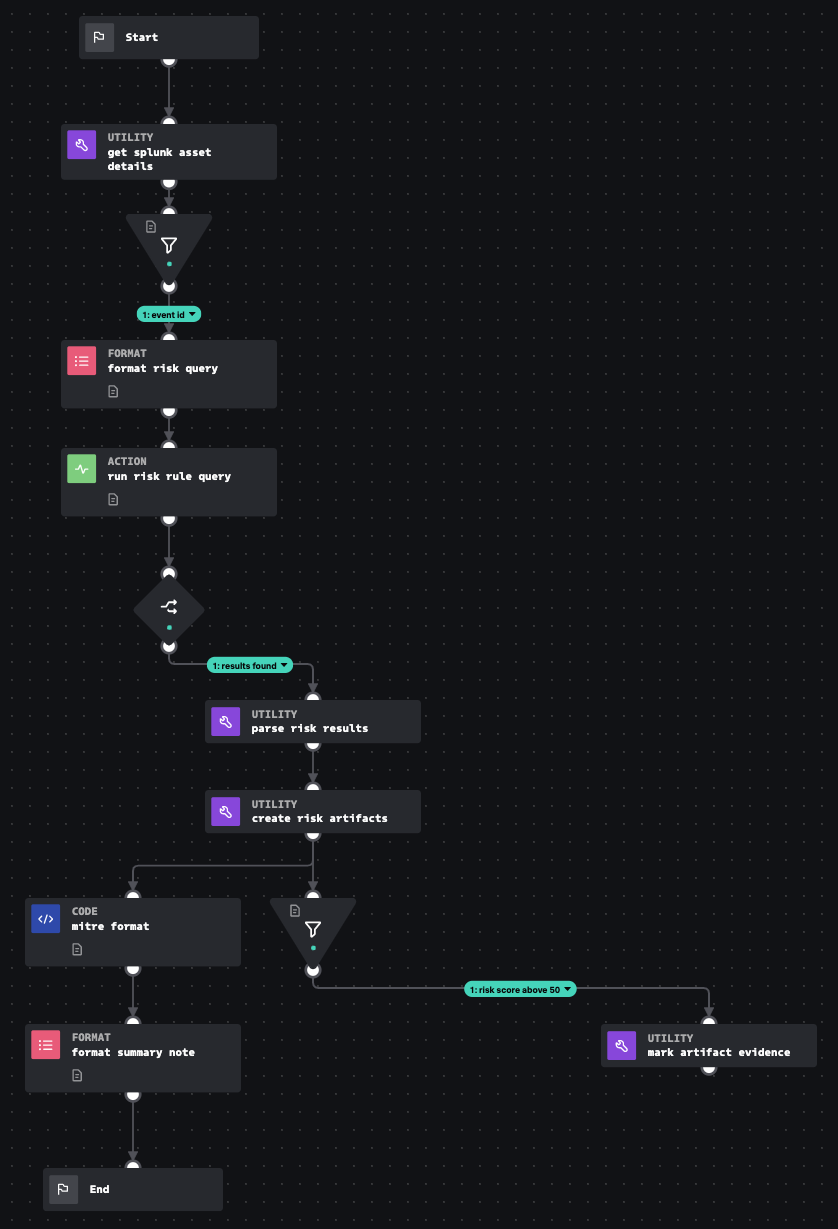
Risk Notable Import Data
Description
This playbook gathers all of the events associated with the risk notable and imports them as artifacts. It also generates a custom markdown formatted note.
- Type: Investigation
- Product: Splunk SOAR
- Apps: Splunk
- Last Updated: 2021-10-22
- Author: Kelby Shelton, Splunk
- ID: 020edc96-ff2b-48b0-9f6f-23da3783fd63
- Use-cases:
Associated Detections
How To Implement
For detailed implementation see https://docs.splunk.com/Documentation/ESSOC/latest/user/Useplaybookpack
Explore Playbook
Required field
- event_id
- info_min_time
- info_max_time
- risk_object
- risk_object_type
Reference
- https://docs.splunk.com/Documentation/ESSOC/latest/user/Useplaybookpack
- http://docs.splunk.com/Documentation/ES/6.6.2/Admin/Configurecorrelationsearches#Use_security_framework_annotations_in_correlation_searches
source | version: 1