Risk Notable Merge Events
Description
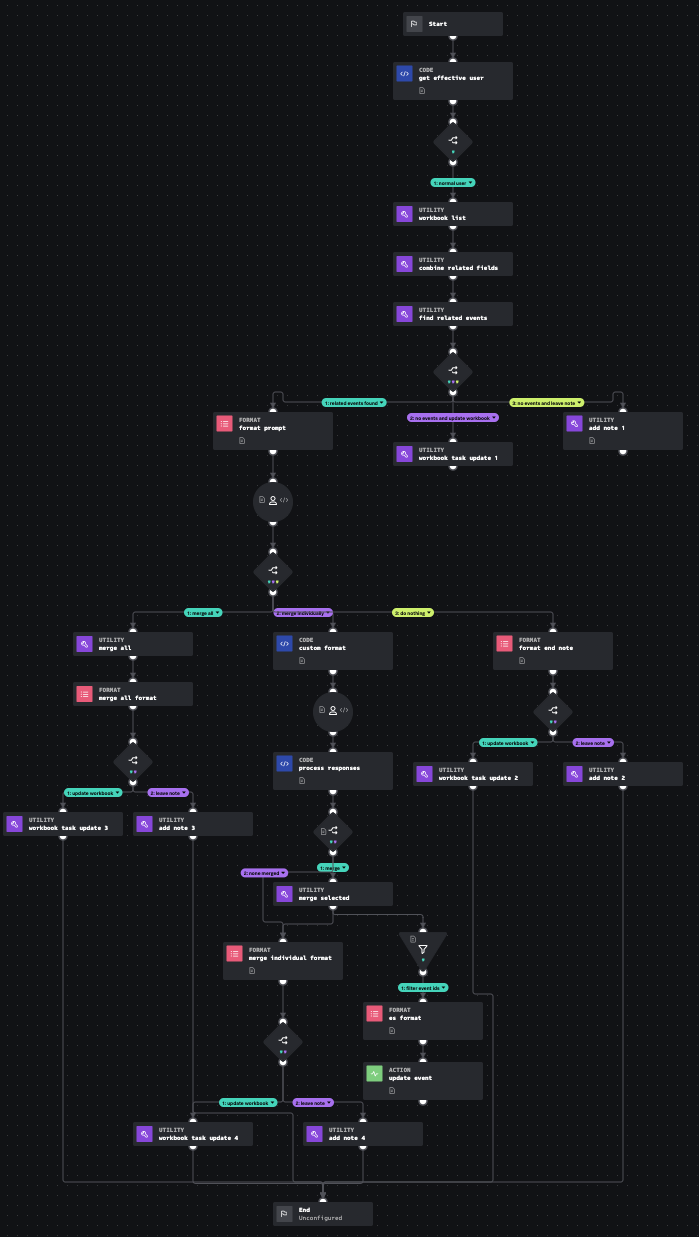
This playbook finds related events based on key fields in a risk notable and allows the user to process the results and decide which events to merge into the current investigation.
- Type: Investigation
- Product: Splunk SOAR
- Apps:
- Last Updated: 2021-10-22
- Author: Kelby Shelton, Splunk
- ID: 040edc96-ff2b-48b0-9f6f-53da3783fd63
- Use-cases:
Associated Detections
How To Implement
For detailed implementation see https://docs.splunk.com/Documentation/ESSOC/latest/user/Useplaybookpack
Explore Playbook
Required field
Reference
source | version: 1