Splunk Message Identifier Activity Analysis
Description
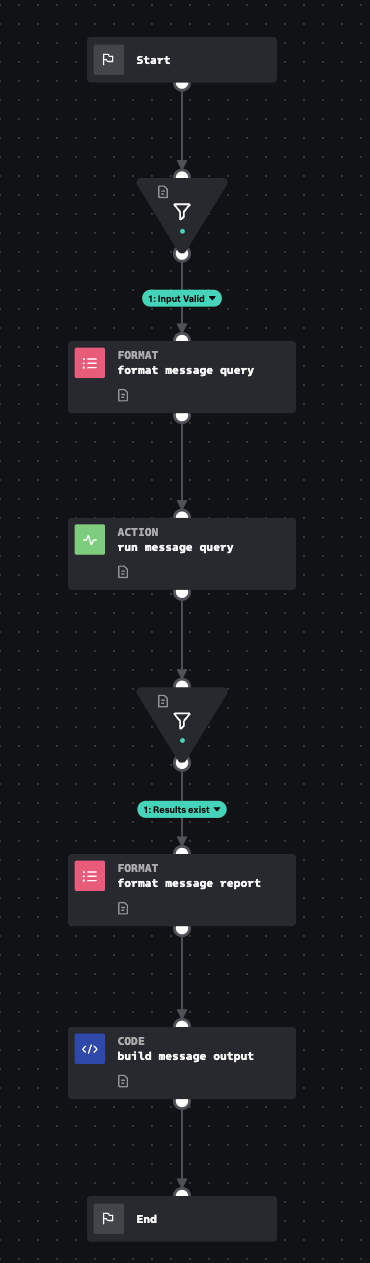
Accepts an internet message id, and asks Splunk to look for records that have a matching internet message id. It then produces a normalized output and summary table.
- Type: Investigation
- Product: Splunk SOAR
- Apps: Splunk
- Last Updated: 2023-01-26
- Author: Lou Stella, Splunk; Kelby Shelton, Splunk
- ID: 5299b9dc-e8c4-46ba-d942-98dae0fa816d
- Use-cases:
- Phishing
Associated Detections
How To Implement
This input playbook requires the Splunk connector to be configured. You will also need data populating the Email.All_Email datamodel in the out-of-the-box configuration of this playbook.
D3FEND
| ID | Technique | Definition | Category |
|---|---|---|---|
| D3-IAA | Identifier Activity Analysis | Taking known malicious identifiers and determining if they are present in a system. | Identifier Analysis |
Explore Playbook
Required field
Reference
source | version: 1