Windows Defender ATP Identifier Activity Analysis
Description
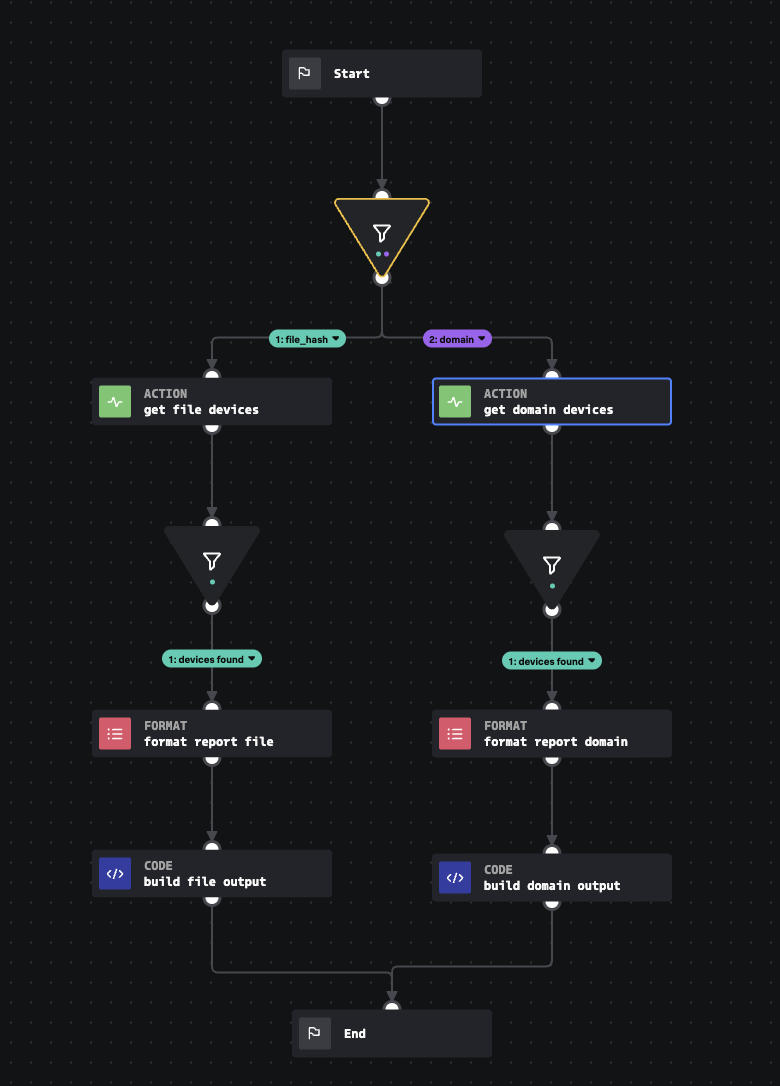
Accepts a file_hash or domain name, and asks Windows Defender ATP for a list of devices that have interacted with each. It then produces a normalized output and summary table.
- Type: Investigation
- Product: Splunk SOAR
- Apps: Windows Defender ATP
- Last Updated: 2023-03-30
- Author: Lou Stella, Splunk
- ID: 5299d9dc-e9c4-46fa-da42-92ace0ff816d
- Use-cases:
- Enrichment
- Endpoint
Associated Detections
How To Implement
This input playbook requires the Windows Defender ATP connector to be configured. It is designed to work in conjunction with the Dynamic Identifier Activity Analysis playbook or other playbooks in the same style.
D3FEND
| ID | Technique | Definition | Category |
|---|---|---|---|
| D3-IAA | Identifier Activity Analysis | Taking known malicious identifiers and determining if they are present in a system. | Identifier Analysis |
Explore Playbook
Required field
Reference
source | version: 1