TruSTAR Enrich Indicators
Description
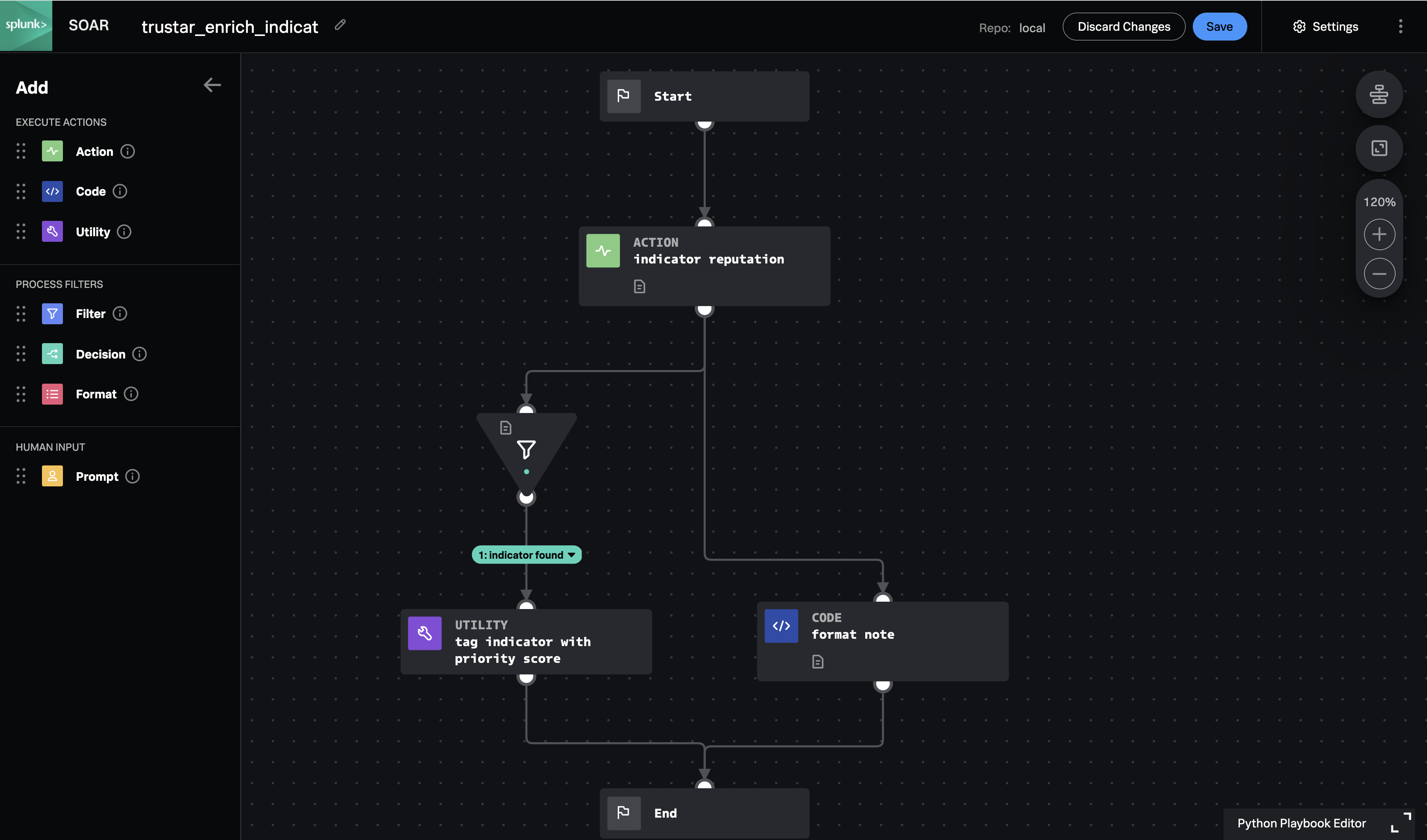
Use TruSTAR to gather threat information about indicators in a SOAR event. Tag the indicators with the normalized priority score from TruSTAR and summarize the findings in an analyst note. This playbook is meant to be used as a child playbook executed by a parent playbook such as "threat_intel_investigate".
- Type: Investigation
- Product: Splunk SOAR
- Apps: TruSTAR
- Last Updated: 2021-11-24
- Author: Philip Royer, Splunk
- ID: fc5adc76-fd2b-48b0-5f6f-63da6423fd63
- Use-cases:
Associated Detections
How To Implement
To use this playbook as a sub-playbook of "threat_intel_investigate", copy it to the local git repository and make sure it has the tags "investigate" and "threat_intel". To use this playbook as a sub-playbook of "risk_notable_enrich", copy it to local and make sure it has the tags "investigate" and "risk_notable" To control the types of indicators processed by this playbook, change the data types of the "indicators" input"
Explore Playbook
Required field
- indicators
Reference
source | version: 1