Internal Host WinRM Log4j Investigate
Description
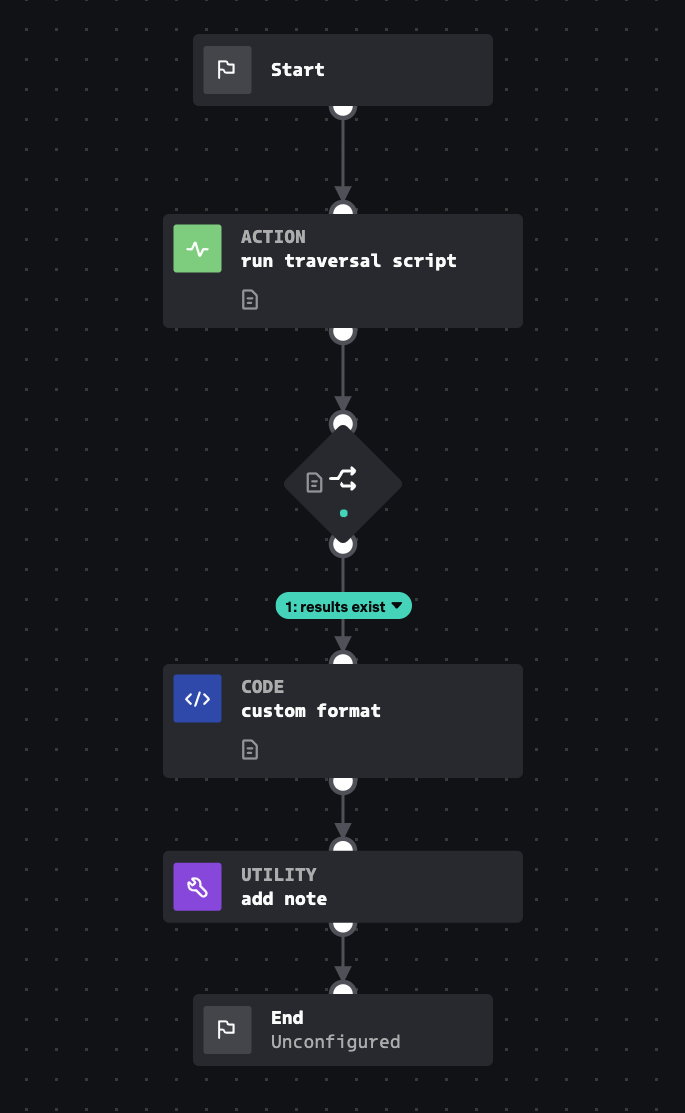
Published in response to CVE-2021-44228, this playbook uses WinRM to scan Windows endpoints for the presence of "jndilookup.class" in all .jar files. The presence of that string could indicate a log4j vulnerability.
- Type: Investigation
- Product: Splunk SOAR
- Apps: Windows Remote Management
- Last Updated: 2021-12-14
- Author: Kelby Shelton, Splunk
- ID: 2cf7c9f4-b273-44f6-a27c-e0db668ff05a
- Use-cases:
Associated Detections
How To Implement
The winrm asset requires Administrator access to scan the whole file system.
Explore Playbook
Required field
Reference
source | version: 1